Application monitoring is a critical aspect of ensuring the optimal performance and security of software systems. Effective monitoring helps to identify and resolve issues before they escalate into major problems that can impact user experience, business operations, and reputation. However, monitoring can be a complex and challenging process, especially in the context of environmental security.
Application monitoring
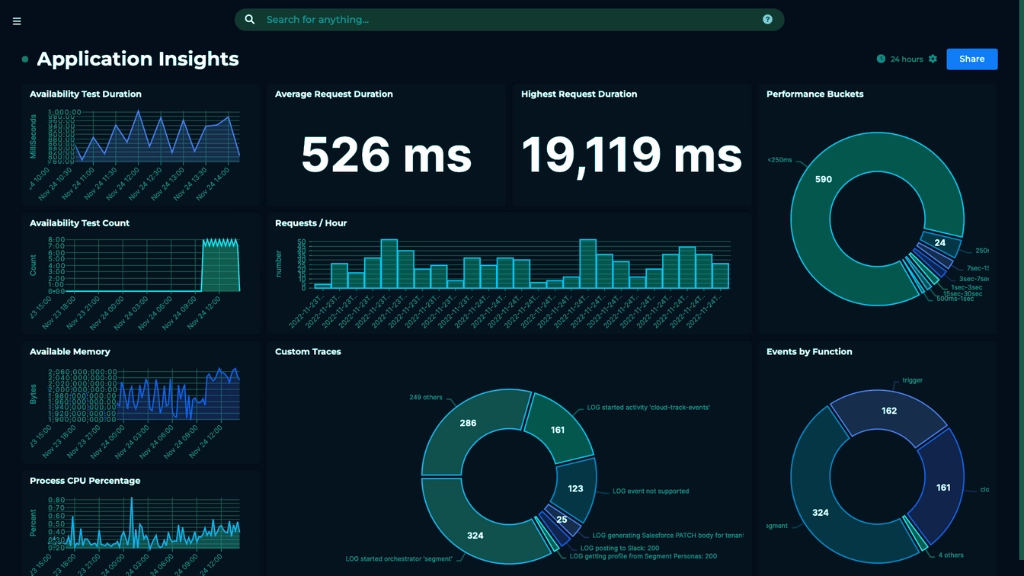
It is the process of monitoring the performance and availability of applications in a data center. It involves collecting data on various metrics, such as response time, CPU usage, memory usage, and network traffic, and analyzing this data to identify any issues or anomalies. Effective application monitoring requires a combination of tools, processes, and best practices.
Best Practices For Machine Learning Applications: A Comprehensive Guide
Application Monitoring Best Practices
Understand Your Applications
The first step in effective application monitoring is to understand your applications. This includes understanding their architecture, dependencies, and performance requirements. By understanding your applications, you can identify the key metrics to monitor and set appropriate thresholds for alerts.
Use the Right Tools
There are many tools available for application monitoring, ranging from simple scripts to complex monitoring platforms. It is important to choose the right tools for your organization’s needs. Some key factors to consider when selecting tools include ease of use, scalability, and integration with other systems.
Monitor Key Metrics
Effective application monitoring requires monitoring key metrics that are relevant to your applications. These metrics may include response time, CPU usage, memory usage, network traffic, and error rates. By monitoring these metrics, you can identify performance issues and take corrective action before they impact your users.
Set Appropriate Thresholds
Setting appropriate thresholds for alerts is critical to effective application monitoring. Thresholds should be based on the performance requirements of your applications and should be set at a level that allows you to detect issues before they impact your users. It is important to regularly review and adjust thresholds as needed.
Monitor Applications in a DMZ
Monitoring applications in a DMZ can be challenging due to security restrictions. However, it is important to monitor these applications to ensure that they are running smoothly and to detect any security breaches. One approach to monitoring applications in a DMZ is to use an agentless monitoring solution.
Use Containers for Application Monitoring
Containers are a lightweight and flexible way to deploy and manage applications. They can also be used for application monitoring, providing a scalable and efficient way to collect and analyze performance data. Containers can be used to monitor both traditional and cloud-native applications.
Computer Vision Applications in Manufacturing
Display Data in a Clear and Actionable Way
Displaying monitoring data in a clear and actionable way is critical to effective application monitoring. This includes using dashboards and reports that provide real-time visibility into the performance of your applications. Dashboards should be designed to highlight key metrics and provide alerts when thresholds are exceeded.
Automate Monitoring Tasks
Automating monitoring tasks can help reduce the workload on IT staff and ensure that monitoring is performed consistently and accurately. This includes automating tasks such as data collection, alerting, and reporting. Automation can also help ensure that monitoring is performed 24/7, even when IT staff are not available.
Integrate Monitoring with Other Systems
Integrating monitoring with other systems, such as incident management and change management, can help ensure that issues are detected and resolved quickly. This includes integrating monitoring with tools such as ServiceNow and Jira, as well as with ITIL processes such as incident management and problem management.
Continuously Improve Monitoring
Effective application monitoring requires continuous improvement. This includes regularly reviewing and updating monitoring processes, tools, and metrics. It also includes analyzing monitoring data to identify trends and areas for improvement. By continuously improving monitoring, organizations can ensure that their applications are running smoothly and efficiently.
Conclusion
Effective application monitoring is critical to modern data center management. By following these best practices, organizations can ensure that their applications are running smoothly and efficiently, and that any issues are detected and resolved quickly. From understanding your applications to continuously improving monitoring, these best practices provide a comprehensive guide to effective application monitoring.
FAQs
What are the benefits of Application monitoring?
The benefits of Application monitoring include improved application performance, increased uptime, reduced downtime, and improved end-user experience.
How can Application monitoring insights be leveraged for the benefit of the business?
Application monitoring insights can be leveraged for the benefit of the business by providing real-time visibility into application performance, which can help business stakeholders make informed decisions about resource allocation, capacity planning, and other critical business decisions.
What are some of the business factors that should be considered when implementing Application monitoring?
Some of the business factors that should be considered when implementing Application monitoring include the criticality of each application and its impact on the business, which will help IT departments prioritize which applications require the most attention.
How can I ensure that my monitoring is performed 24/7?
Monitoring can be performed 24/7 through the use of automation and the use of monitoring tools that provide real-time alerts.