In today’s digital age, web applications are becoming increasingly popular, and so are the risks associated with them. Cybercriminals are always on the lookout for vulnerabilities in web applications that they can exploit to gain unauthorized access to sensitive data. To mitigate these risks, organizations need to implement robust security solutions that can protect their web applications from various types of attacks. Two such solutions are Runtime Application Self-Protection (RASP) and Web Application Firewall (WAF).
What is RASP?
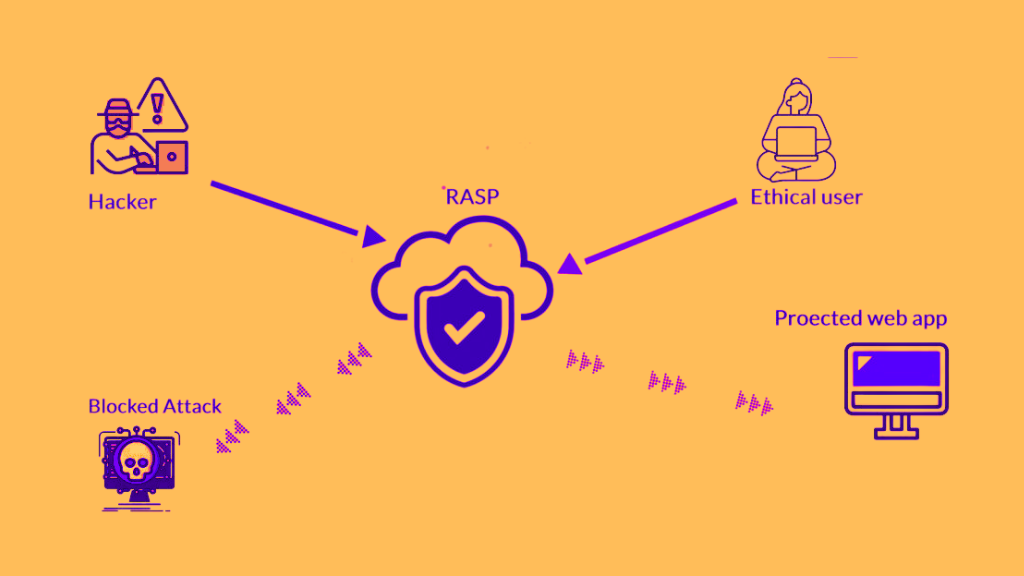
Runtime Application Self-Protection (RASP) is a security solution that provides real-time protection to web applications by monitoring their runtime behavior. RASP works by embedding security controls within the application itself, which allows it to detect and prevent attacks before they can cause any damage. RASP is proactive in nature and can identify and mitigate risks before they are exploited by attackers on vulnerable applications or their data.
RASP uses various techniques such as dynamic analysis, behavioral analysis, and machine learning to detect and prevent attacks. Dynamic analysis involves monitoring the runtime behavior of the application to detect any abnormal activity. Behavioral analysis involves analyzing the behavior of the application to detect any suspicious activity. Machine learning involves using algorithms to learn from past attacks and predict future attacks.
Cybersecurity vs Software Engineering: Choosing the Right Career Path
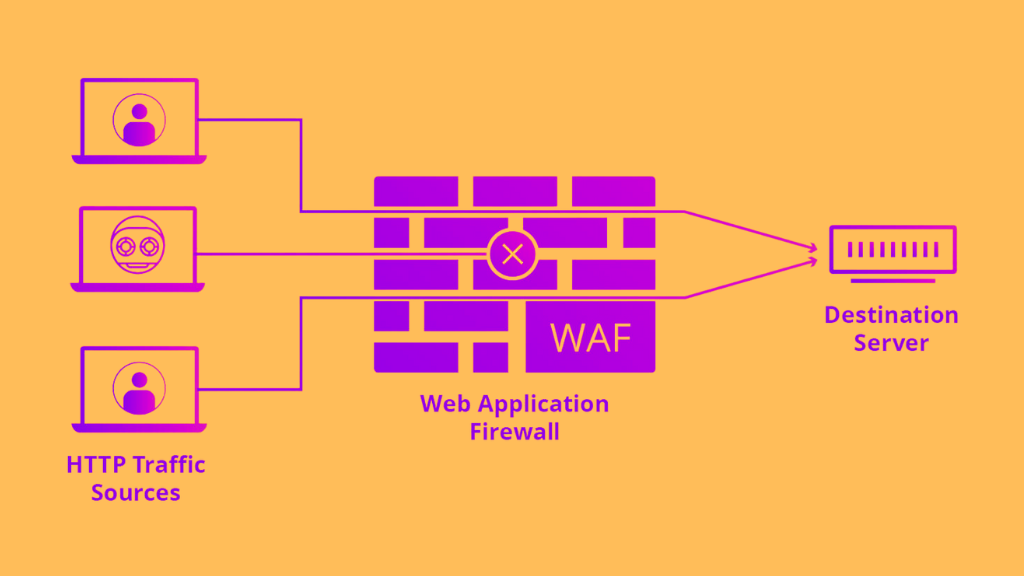
What is WAF?
Web Application Firewall (WAF) is a security solution that provides protection to web applications by analyzing the traffic between the application and the user. WAF works by filtering out malicious traffic and blocking it from reaching the application. WAF is reactive in nature and can only detect and prevent attacks that have already been identified as malicious. WAF uses various techniques such as signature-based detection, anomaly-based detection, and reputation-based detection to detect and prevent attacks.
Signature-based detection involves comparing the traffic against a database of known attack signatures. Anomaly-based detection involves analyzing the traffic to detect any abnormal activity. Reputation-based detection involves analyzing the reputation of the traffic source to determine if it is trustworthy or not.
RASP vs WAF: How do they compare?
Now that we have a basic understanding of RASP and WAF, let’s compare them based on various parameters.
Detection Mechanism
RASP detects attacks by monitoring the runtime behavior of the application, whereas WAF detects attacks by analyzing the traffic between the application and the user. RASP is more proactive in nature and can detect and mitigate risks before they are exploited by attackers. WAF, on the other hand, is more reactive in nature and can only detect and prevent attacks that have already been identified as malicious.
Protection Against New Vulnerabilities
RASP provides protection against new application vulnerabilities that are not present in WAF. RASP can be used to defend legacy applications or those that have been developed for operating systems other than Windows. WAF, on the other hand, requires an organization to know what vulnerabilities are out there in order to build their defense against them.
Performance Impact
RASP has a lower performance impact than WAF because it embeds security controls within the application itself. This means that RASP does not require additional hardware resources to function, and it does not add any latency to the application. WAF, on the other hand, can have a significant impact on performance because it analyzes the traffic between the application and the user, which can cause latency and slow down the application.
False Positives and False Negatives
RASP has a lower rate of false positives and false negatives than WAF. This is because RASP monitors the runtime behavior of the application, which allows it to detect and prevent attacks more accurately. WAF, on the other hand, can generate false positives and false negatives because it analyzes the traffic between the application and the user, which can be affected by various factors such as network latency, user behavior, and more.
Ease of Deployment and Maintenance
RASP is easier to deploy and maintain than WAF. This is because RASP embeds security controls within the application itself, which means that it does not require any additional hardware or software to function. WAF, on the other hand, requires an organization to deploy and maintain a separate hardware or software appliance, which can be time-consuming and costly.
How to Start a Career in CyberSecurity?
Cost
RASP is generally more expensive than WAF. This is because RASP requires an organization to embed security controls within the application itself, which can be a complex and time-consuming process. WAF, on the other hand, is generally less expensive than RASP because it requires an organization to deploy and maintain a separate hardware or software appliance, which is less complex and time-consuming.
Conclusion
In conclusion, both RASP and WAF are effective security solutions that can protect web applications from various types of attacks. However, they differ in their detection mechanism, protection against new vulnerabilities, performance impact, false positives and false negatives, ease of deployment and maintenance, and cost. Organizations should carefully evaluate their security needs and choose the solution that best meets their requirements. If an organization needs proactive protection against new vulnerabilities and has the resources to embed security controls within the application itself, RASP may be the better solution.
If an organization needs reactive protection against known vulnerabilities and has limited resources, WAF may be the better solution. It is also worth noting that RASP and WAF can complement each other, and organizations can use both solutions to provide comprehensive protection to their web applications.
FAQs
How does RASP work?
RASP works by embedding security controls within the application itself, which allows it to detect and prevent attacks before they can cause any damage.
Which one is more proactive in nature, RASP or WAF?
RASP is more proactive in nature because it can identify and mitigate risks before they are exploited by attackers on vulnerable applications or their data.
What are some limitations that may limit the effectiveness of RASP?
Some common limitations of RASP include limited hardware resources available on IoT devices or small file sizes which could lead to false negatives with regular expression matching logic. In addition, buffer overflow attacks can be difficult if not impossible to defend against when using static code emulation over dynamic runtime analysis techniques.
How does RASP compare to WAF?
RASP and WAF are both effective security solutions that can protect web applications from various types of attacks. However, they differ in their detection mechanism, protection against new vulnerabilities, performance impact, false positives and false negatives, ease of deployment and maintenance, and cost. Organizations should carefully evaluate their security needs and choose the solution that best meets their requirements.